Introduction
In today's fast-paced and highly interconnected digital landscape, maintaining the security of sensitive information is crucial for businesses of all sizes. The widespread adoption of cloud technology and mobile devices has led to an increased need for effective identity and access management (IAM) solutions that can provide robust protection against potential security threats.
Whether you prefer to watch a video or dive deep into a blog post, we've got you covered! Our latest video covers the topic at hand in detail, and we also have a comprehensive blog post available for those who prefer to read.
IAM is the foundation of any effective security strategy, and it involves controlling access to digital resources and ensuring that users are who they claim to be. In this blog series, we will explore the various aspects of Microsoft 365 for Enterprise security, starting with IAM. We will look at the various tools and features available within the Microsoft 365 suite that can help businesses protect their digital assets and prevent unauthorized access. By implementing these solutions, businesses can improve their security posture and reduce the risk of costly security breaches.
Dedicated Global Administrator Accounts with MFA and PIM
In any organization, there are individuals who are granted full access to the company's Microsoft 365 environment, commonly referred to as global administrator accounts. These accounts are used to manage various aspects of the Microsoft 365 environment, including user accounts, security policies, and data access. As global administrator accounts have such broad control, they are often targeted by hackers as a primary entry point into an organization's systems.
To mitigate the risk of global administrator account compromise, Microsoft recommends using dedicated global administrator accounts, separate from an individual's day-to-day user account. This ensures that the global administrator account is only used when necessary, reducing the risk of an accidental or malicious compromise. Additionally, using a dedicated global administrator account helps to segregate duties and responsibilities, providing an extra layer of control.
To further secure dedicated global administrator accounts, Microsoft recommends using Multi-Factor Authentication (MFA) and Microsoft Privileged Identity Management (PIM). MFA provides an additional layer of security by requiring a second form of authentication, such as a text message or phone call when attempting to access the global administrator account. PIM helps to manage and monitor the use of privileged accounts, providing just-in-time access and temporary, time-bound access to reduce the risk of permanent account misuse.
Feature | Multi-Factor Authentication (MFA) | Privileged Identity Management (PIM) |
|---|---|---|
Purpose | Protects user accounts | Manages access to privileged accounts |
Authentication | Requires multiple forms of verification (e.g., password and mobile phone code) | No authentication, but manages privileges |
Application | Applicable to all user accounts | Applicable to privileged accounts only |
Security | Helps prevent unauthorized access to user accounts | Helps prevent the misuse of privileged accounts |
Benefits | Increases security for all user accounts | Provides an extra layer of security for privileged accounts |
Management | Easy to manage and configure | Can be complex to manage and configure |
Implementation | Relatively simple to implement | Requires a dedicated system and setup |
Cost | Included in most Microsoft 365 plans | Requires an additional license or subscription |
It's important to note that MFA and PIM are not mutually exclusive - they can be used together to provide an even higher level of security.
By implementing dedicated global administrator accounts with MFA and PIM, organizations can reduce the risk of global administrator account compromise, helping to protect their Microsoft 365 environment and the sensitive data it contains.
MFA for All User Accounts
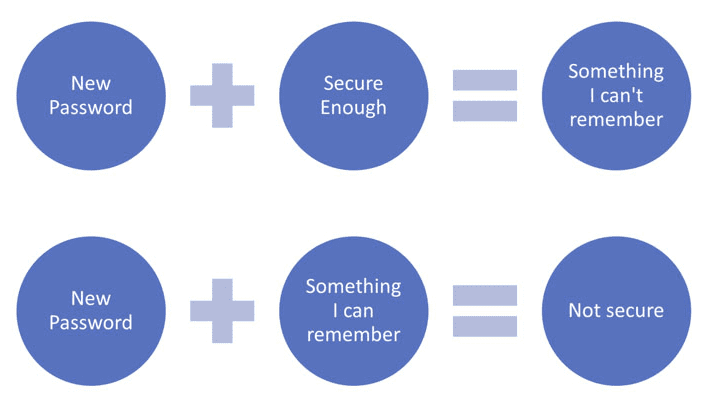
Multi-factor authentication (MFA) is an essential tool for securing user accounts in today's digital landscape. What is multi-factor authentication? It's a security measure that requires users to provide additional forms of authentication beyond a username and password, such as a fingerprint or a code sent to their mobile device, before accessing sensitive data or systems. This extra layer of security makes it much more difficult for attackers to gain unauthorized access to an organization's resources.
In the context of Microsoft 365 for Enterprise security, MFA can be applied to all user accounts. This means that in addition to the primary username and password, users are required to provide another form of authentication before being granted access to Microsoft 365 applications and services. This can include Outlook, OneDrive, SharePoint, Teams, and more.
Implementing MFA solutions for all user accounts can significantly improve an organization's security posture. By requiring an additional layer of authentication for all users, even if an attacker has obtained a user's password through a phishing attack or othermeans, they will not be able to gain access to sensitive data or systems without the second factor of authentication.
Microsoft offers several types of MFA options to choose from, including SMS codes, mobile app notifications, phone calls, hardware tokens, and biometric factors such as fingerprints and facial recognition. Best practices for implementing MFA include selecting the appropriate factors of authentication for your organization, ensuring all users are enrolled in MFA and using conditional access policies to require MFA for specific applications or locations.
Overall, implementing MFA conditional access policy for all user accounts is a crucial step in enhancing an organization's security posture and protecting against unauthorized access to sensitive data and systems.
Safer Device and Application Access with Conditional Access policies
Safer device and application access is a critical component of any modern cloud identity and access management (IAM) strategy. One of the most effective ways to achieve this is by using Conditional Access policies, which allow organizations to control access to apps and data based on a user's device, location, and other factors.
Conditional Access policies work by creating rules that govern how users can access resources based on certain criteria. For example, a policy may require that a user has MFA enabled on their device before they can access a specific application. These policies can be customized to meet the unique needs of your organization and can be applied to several types of resources, including on-premises and cloud-based apps.
There are many benefits to using Conditional Access policies, including increased security, improved user experience, and greater control over data access. By enforcing strict access policies, organizations can reduce the risk of data breaches and other security threats. Conditional Access policies also enable more secure access from personal devices, which can increase productivity and employee satisfaction.
Creating and configuring Conditional Access policies in Microsoft 365 is a straightforward process. Administrators can use the Azure Active Directory portal to define the rules and conditions that will govern access to apps and data. The portal provides a range of built-in templates and policies that can be customized to meet your organization's specific needs.
Real-world use cases for Conditional Access policies include restricting access to sensitive data from outside the organization, requiring MFA for high-risk transactions, and limiting access to corporate resources from untrusted devices. By implementing the Conditional Access policy azure, organizations can significantly reduce the risk of data breaches and other security incidents, while also improving the overall security posture of their IT environment.
Windows Hello for Business
Windows Hello for Business is a feature in Microsoft 365 that provides a secure, passwordless way to access devices, apps, and services. Windows Hello for Business replaces traditional passwords with strong, multi-factor authentication using biometrics such as facial recognition, fingerprints, and PINs. Here are some key features and benefits of Windows Hello for Business:- Increased security: With Windows Hello for Business, users can access their devices and apps with a simple, secure gesture or PIN, eliminating the need for complex passwords that can be easily forgotten or hacked. This provides a higher level of security, reducing the risk of unauthorized access to sensitive information.
- Enhanced user experience: Windows Hello for Business provides a seamless, intuitive user experience. Users can sign in quickly and easily using biometrics, without the need to remember passwords or type in lengthy usernames.
- Simplified management: Windows Hello for Business can be centrally managed through the Azure Active Directory, providing a simple and secure way to manage devices and authentication policies across an organization.
- Compatibility: Windows Hello for Business works across a range of devices and platforms, including Windows 10, iOS, and Android.
- Easy setup: Setting up Windows Hello passwordless solution is easy and can be done in a few simple steps. Users can enroll their biometric data, set up a PIN, and start using Windows Hello for Business to access their devices and apps.
Overall, Windows Hello for Business is a highly secure, easy-to-use solution for accessing devices, apps, and services in Microsoft 365. With its strong multi-factor authentication service, simplified management, and compatibility with a range of devices and platforms, it offers a seamless and secure user experience that helps organizations protect sensitive information and enhance productivity.
Windows Defender Credential Guard
Windows Defender Credential Guard is a security feature that is designed to protect user credentials from being stolen or compromised. It is available on Windows 10 Enterprise and Windows Server 2016, and it uses virtualization-based security to protect sensitive data.
The basic idea behind Credential Guard is to protect user authentication credentials from being stolen by malware or attackers. This includes things like NTLM hashes, Kerberos tickets, and certificates. When a user logs in to their system, their credentials are stored in memory where attackers can easily access them. By using virtualization-based security, Credential Guard can protect these credentials from being stolen or compromised.
Credential Guard works by creating a secure isolated environment called the "security kernel" that runs separately from the operating system. This security kernel is responsible for storing user authentication credentials and protecting them from unauthorized access. By separating the security kernel from the rest of the system, attackers are unable to steal or tamper with user credentials even if they manage to compromise the operating system.
In addition to protecting user credentials, the Credential Guard also protects against pass-the-hash attacks. This is a common attack method used by attackers to steal passwords and gain unauthorized access to systems. With Credential Guard, pass-the-hash attacks are much more difficult to carry out because the user's password is not stored in memory where it can be easily accessed.
To use Credential Guard, you need to have a compatible hardware platform and enable the feature in the system BIOS. You also need to run a supported operating system and have the appropriate security policies in place. Once enabled, Credential Guard is a powerful security feature that can provide additional protection against a range of common attack methods.
Get help implementing Identity and Access Management
In today's digital landscape, protecting digital identities and access is of utmost importance. IAM plays a crucial role in ensuring that only authorized personnel can access sensitive data and applications, and Microsoft 365 offers a range of IAM solutions and strategies to help you achieve this.
In this blog post, we've explored the importance of using dedicated global administrator accounts with MFA and PIM, implementing MFA for all user accounts, and leveraging Conditional Access policies, Windows Hello for Business, and Windows Defender Credential Guard to enhance device and application security.
Communication Square is a preferred Microsoft Gold Partner and can help you implement these Identity and access management solutions and strategies in your organization. We can also provide you with best practices for implementing IAM and protecting your digital assets.
You can find parts 2, 3, and 4 of our blog series listed below, where we'll explore Microsoft 365 solutions for threat protection, information protection, and security management.
Contact us today to learn more about how we can help you implement IAM solutions and protect your organization from potential security threats.
Last Updated 2 months ago


