The Imperative of Protecting Privileged Accounts
Imagine your organization's most sensitive data as the crown jewels—priceless, irreplaceable, and highly coveted by those with ill intent. Privileged accounts, protected by advanced identity protection, are the keys to this treasure trove, offering access to everything from confidential files to critical system controls. Yet, all too often, these keys are left hanging on a hook by the door, just waiting to be snatched up by the wrong hands.
With cyber threats evolving at a breakneck pace, relying on outdated security measures is like guarding your crown jewels with a rusty old padlock. Hackers are smarter, faster, and more determined than ever, and they’re specifically targeting those privileged accounts. Why? Because these accounts hold the keys to your kingdom—granting access to modify permissions, create backdoor accounts, or even delete critical data.
For Small and Medium-Sized Businesses (SMBs), the stakes couldn’t be higher. A single compromised account could lead to catastrophic breaches, legal repercussions, and a loss of trust that’s nearly impossible to rebuild. That’s why advanced identity protection isn’t just a luxury—it’s a necessity. It’s about staying one step ahead of cyber adversaries and ensuring that your organization’s most valuable assets are shielded by more than just hope and a prayer. Just like implementing the best identity theft protection solutions for personal data, protecting privileged accounts in your organization is about staying one step ahead of cyber adversaries and ensuring that your most valuable assets are shielded by more than just hope and a prayer.
Understanding Privileged Accounts and Their Risks
What Makes Privileged Accounts So Special
Privileged accounts are the VIPs of your organization's digital ecosystem. These are the accounts with elevated permissions, granting their users significant control over systems, access to restricted information, and the ability to make changes that can affect the entire organization. Think of them as the command centers—whether it’s modifying security settings, creating new user accounts, or accessing highly sensitive data, privileged accounts hold the keys to your company’s most critical resources.
But with great power comes great responsibility—and, unfortunately, great risk. Because these accounts have such extensive access, they are incredibly appealing to cybercriminals. If a hacker manages to compromise a privileged account, they can essentially operate with the same level of access as a top-level administrator, leading to potentially devastating consequences.
Just as theft insurance credit bureau monitoring helps protect individuals by detecting identity theft early, businesses need to monitor and protect privileged accounts to prevent malicious access. Monitoring these accounts, much like monitoring credit reports, can help catch unusual activity and avoid long-term damage.
Different Flavors of Privileged Accounts
Not all privileged accounts are created equal. They vary in scope, task, and, of course, risk. Let’s break down the different types:
Domain Admin Accounts:
These are the big ones. Domain Admins have complete control over the domain and all its resources. They can manage all domain-oriented settings, create or delete user accounts, enforce security policies, and access or monitor all servers and computers within the domain. With such extensive control, these accounts are considered high-risk targets. For more on securing these types of accounts, you can check out our detailed guide on Microsoft 365 for Enterprise Security.
Local Administrative Accounts:
These accounts allow administrative access to individual systems. Users can install and manage software, change system settings, and control user accounts on a specific machine. While they pose a moderate risk, mismanagement of these accounts can lead to serious vulnerabilities. Learn more about securing local administrative accounts in our blog post on Setting Up Microsoft 365 Identity Protection.
Service Accounts:
Service accounts are used by applications to interact with operating systems. Initially granted broad permissions, these accounts should be carefully restricted to only what’s necessary for service operation. They carry a moderate risk, particularly if the service they support is compromised. For additional protection, consider implementing Multi-Factor Authentication (MFA) as a security measure.
Database Admin Accounts:
These accounts are responsible for overseeing and managing databases. They can create and modify databases, control database user accounts, and provide access-based permissions. Given the sensitivity of the data they handle, database admin accounts are high-risk and require stringent protection. Discover how Microsoft Entra ID can help secure these accounts.
Network Admin Accounts:
Network Admins manage and oversee the network infrastructure. They can configure any device connected to the network, manage network security and firewalls, and monitor network traffic. While moderate-risk, if compromised, these accounts could lead to a network-wide security breach and significant data loss. For best practices, explore our insights on Unlocking Microsoft Active Directory.
Application Accounts:
These accounts are focused on the control and management of specific applications. Though their permissions are limited to individual applications, poor configuration can elevate their permissions, leading to application-level vulnerabilities that could compromise data and functionality. For guidance on securing application accounts, refer to Microsoft’s guidelines on application management.
Why Hackers Love Privileged Accounts
So, why are these accounts such juicy targets? It’s all about access. A compromised privileged account is a golden ticket for hackers, offering them the ability to navigate through your organization’s most sensitive areas undetected. With control over critical systems, data, and security settings, a hacker could cause massive disruption, steal confidential information, or even bring down entire networks.
For SMBs, the risks are even greater. Without the extensive security measures that larger enterprises might have, SMBs often struggle to manage these accounts effectively. And when privileged accounts are compromised, the fallout can be catastrophic—ranging from financial losses to severe reputational damage. Much like individuals searching for the best price id theft insurance credit solutions to protect their personal identity, SMBs must find affordable and effective ways to secure privileged accounts without breaking the bank.
Advanced Tactics to Shield Your Privileged Accounts
When it comes to protecting your organization’s most valuable digital assets, standard security measures just won’t cut it. Hackers are continuously evolving, finding new ways to slip past traditional defenses. This is where advanced identity protection tactics come into play, offering a robust line of defense that can adapt to the ever-changing threat landscape.
Just like evaluating insurance credit bureau monitoring price when protecting personal identity, businesses need to carefully assess the cost and effectiveness of the security measures they implement for privileged accounts. With the right strategy, the investment in identity protection becomes invaluable compared to the potential fallout of a breach.
Here’s a deep dive into the most effective strategies for safeguarding your privileged accounts:
Multi-Factor Authentication (MFA): A Necessary Layer
Gone are the days when a simple password was enough to protect your accounts. Multi-Factor Authentication (MFA) is now a must-have for any organization serious about security. MFA requires users to provide multiple forms of verification—something they know (like a password), something they have (such as a smartphone), and something they are (biometric data like a fingerprint). This additional layer makes it significantly harder for unauthorized users to gain access. According to a report by Microsoft, MFA can block over 99.9% of account compromise attacks.
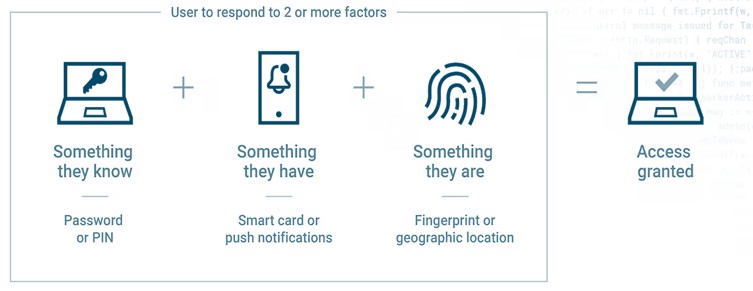
Implementing MFA across all privileged accounts is a simple yet powerful step toward enhanced security. Tools like Microsoft Entra ID provide integrated MFA solutions that work seamlessly with your existing infrastructure.
Behavioral Analytics: Spotting the Insider Threats
While MFA is great for keeping out external attackers, what about the threats that come from within? That’s where behavioral analytics comes into play. By analyzing the normal behavior of users—such as login times, access patterns, and the types of files they interact with—behavioral analytics can identify unusual activity that may indicate a compromised account or an insider threat.
For example, if a user who typically logs in from the office during regular hours suddenly accesses the system from an unfamiliar location in the middle of the night, this anomaly can trigger an alert. Behavioral analytics doesn’t just react to threats; it proactively identifies them before they can cause significant damage. This tactic is especially effective when integrated with solutions like Microsoft 365's Threat Intelligence, which offers advanced monitoring and alerting capabilities.
Privileged Access Management (PAM): Control and Monitor
Privileged Access Management (PAM) is like having a bouncer at the door of your digital fortress. PAM solutions control and monitor activities of privileged accounts, ensuring that access is limited to only those who truly need it, and that every action is logged and auditable. This approach not only limits potential damage but also provides a clear trail of who did what and when.
Consider using tools like Microsoft’s PAM solutions to implement stricter controls over your privileged accounts. These tools help in automating the approval processes for access requests and enforce the principle of least privilege, ensuring users only have the access necessary for their role—nothing more, nothing less.
Biometric Verification: The Personal Touch
Passwords can be stolen, and devices can be lost, but biometric data is unique to each individual. Biometric verification, such as fingerprint scans, facial recognition, or even retinal scans, adds a personal touch to security. This method provides an extra layer of protection that’s incredibly difficult to forge.
Integrating biometric verification into your access management strategy is a forward-thinking move that aligns with the latest advancements in security technology. Tools like Microsoft Authenticator offer built-in biometric options, making it easier to enhance your security without overcomplicating the user experience.
Real-Time Monitoring: Staying One Step Ahead
In the fast-paced world of cybersecurity, real-time monitoring is essential. This tactic involves continuously overseeing user activities to detect and respond to threats as they happen. Whether it’s automated alerts for suspicious activity or the ability to lock down an account at the first sign of trouble, real-time monitoring is about staying one step ahead of potential breaches.
By incorporating real-time monitoring into your security strategy, you can ensure that your privileged accounts are under constant surveillance, making it far more difficult for unauthorized access to go unnoticed. Azure Security Center is a great example of a tool that provides real-time monitoring and threat detection, integrating seamlessly with your existing Microsoft environment.
Session Management and Supervision: Keeping an Eye on Things
Effective session management includes monitoring, controlling, and even terminating privileged sessions as necessary. By setting up session time-outs, recording sessions for audits, and having a comprehensive tool for managing and reviewing session activities, you add yet another layer of security to your privileged accounts.
Session management ensures that even if a session is left open accidentally, it doesn’t become a gateway for unauthorized access. Solutions like Microsoft 365’s Session Management Tools offer features that help you stay in control, even in dynamic and complex environments.
Spotlight on Microsoft Entra ID for Privileged Identity Protection
When it comes to advanced identity protection, Microsoft Entra ID (formerly known as Azure Active Directory) is leading the charge with a suite of tools specifically designed to secure your organization’s privileged accounts. In a world where cyber threats are becoming increasingly sophisticated, Entra ID offers a robust framework that not only protects but also enhances your overall security posture.
Key Features That Set Entra ID Apart
Microsoft Entra ID isn’t just another identity management tool—it’s a comprehensive security solution that integrates seamlessly with your existing Microsoft ecosystem. Here’s how it can fortify your defenses:
- Multi-Factor Authentication (MFA): As mentioned earlier, MFA is critical for preventing unauthorized access. Entra ID simplifies the implementation of MFA across your organization, ensuring that all privileged accounts are protected with an additional layer of security. It’s not just about passwords anymore—Entra ID allows you to leverage biometric verification and device-based authentication for enhanced protection.
- Conditional Access Policies: One of the standout features of Entra ID is its ability to enforce Conditional Access policies. These policies allow you to control access to resources based on specific conditions, such as user location, device compliance, or risk level. For instance, you can set policies that require MFA only when users are accessing resources from outside your corporate network. This level of granularity ensures that your security measures are both effective and user-friendly.
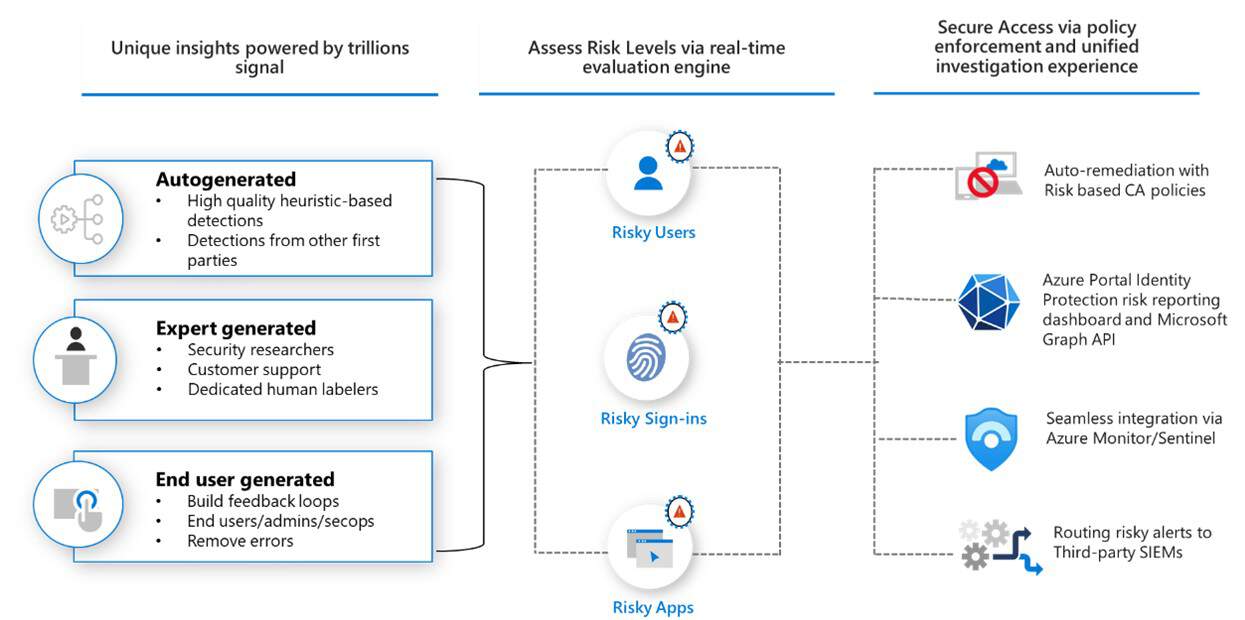
- Privileged Identity Management (PIM): Entra ID includes Privileged Identity Management (PIM) features that help you manage, control, and monitor access to critical resources. PIM allows you to enforce just-in-time access for privileged roles, meaning users can only elevate their permissions when absolutely necessary—and only for a limited time. This drastically reduces the risk of privilege misuse.
- Real-Time Threat Detection: With Entra ID’s real-time threat detection capabilities, you can stay ahead of potential breaches. The system continuously monitors for unusual activities and provides automated alerts, allowing you to respond to threats as they emerge. This proactive approach is crucial for maintaining the security of your privileged accounts.
- Seamless Integration with Microsoft 365: Entra ID is designed to work hand-in-hand with other Microsoft services like Microsoft 365, ensuring a unified approach to security. This integration allows you to manage identity and access across your entire IT environment from a single platform, making it easier to enforce security policies and monitor compliance.
Why Entra ID Is a Game Changer for SMBs
For Small and Medium-Sized Businesses (SMBs), the cost and complexity of implementing robust security solutions can be a significant barrier. However, Microsoft Entra ID levels the playing field by offering enterprise-grade security that’s scalable to the needs of SMBs. It’s designed to provide comprehensive protection without the need for an army of IT specialists to manage it.
By integrating Entra ID into your security strategy, you gain access to a powerful suite of tools that can protect your privileged accounts from both internal and external threats. Whether you’re operating in a traditional enterprise environment, leveraging cloud platforms, or using a hybrid configuration, Entra ID offers the flexibility and security you need to keep your organization safe.
Rigorous Control with Identity Access Management (IAM)
At the core of Entra ID is its Identity Access Management (IAM) framework, which allows organizations to control who has access to what resources and under what conditions. This is particularly crucial for privileged accounts, where the stakes are high, and the risks are significant. With Entra ID, you can:
- Implement Least Privilege Access: Entra ID’s IAM enables you to enforce the principle of least privilege, ensuring that users only have the access necessary for their roles. This minimizes the attack surface and reduces the chances of privilege escalation.
- Automate Access Requests: Managing access requests manually can be time-consuming and prone to error. Entra ID allows you to automate these processes, ensuring that access is granted only after proper authorization and in line with your organization’s policies.
- Monitor Access in Real-Time: Continuous monitoring of access patterns is essential to identifying and responding to threats as they happen. Entra ID provides real-time insights into who is accessing what, when, and from where, enabling you to detect anomalies before they become incidents.
Comprehensive Protection Across Environments
One of the challenges many organizations face is securing privileged accounts across diverse environments—be it on-premises, in the cloud, or a mix of both. Entra ID excels in providing unified protection across all these environments:
Unified Security Policies: With Entra ID, you can enforce consistent security policies across your entire organization, regardless of where your resources are located. This ensures that all privileged accounts are subject to the same stringent security controls, whether they’re on-premises or in the cloud.
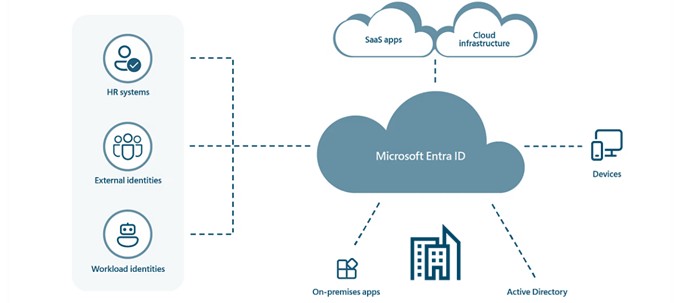
Hybrid Identity Management: Entra ID has enhanced its hybrid identity management capabilities, making it easier to manage identities and access across mixed environments. This includes seamless integration with on-premises Active Directory and other identity providers, allowing for a more streamlined and secure identity management experience.
Advanced Reporting and Analytics: To make informed decisions, you need access to detailed reports and analytics on how your privileged accounts are being used. Entra ID provides comprehensive reporting tools that give you a clear view of access trends, potential risks, and compliance status.
Communication Square LLC’s Expertise in Identity Protection
When it comes to safeguarding your organization’s privileged accounts, choosing the right partner can make all the difference. At Communication Square LLC, we specialize in advanced identity protection solutions tailored to the unique needs of Small and Medium-Sized Businesses (SMBs). With a deep understanding of Microsoft Entra ID and a proven track record of success, we’re here to help you navigate the complexities of identity management and secure your most valuable digital assets.
Why Choose Communication Square LLC?
- Expertise in Microsoft Technologies: As a trusted Microsoft Partner, we have extensive experience in deploying and managing Microsoft Entra ID and other Microsoft security solutions. Our team stays up-to-date with the latest developments, ensuring that you benefit from the most advanced identity protection features available.
- Proven Success: We’ve helped numerous SMBs across various industries enhance their security posture and protect their privileged accounts. Our clients trust us to deliver results, and we take that responsibility seriously.
- Customer-Centric Approach: Your success is our success. We prioritize your needs and work collaboratively to develop solutions that not only meet but exceed your expectations. Our goal is to build long-term relationships based on trust, transparency, and mutual success.
Take the Next Step in Securing Your Privileged Accounts
Protecting your organization’s privileged accounts is critical to maintaining the integrity and security of your entire digital infrastructure. With Communication Square LLC as your partner, you can rest assured that your identity protection strategy is in expert hands.
Ready to take the next step? Schedule a consultation and learn how we can help you implement advanced identity protection solutions tailored to your business.
Last Updated 2 months ago
