Vital Signs: Endpoint Security 2025 - Stats That Demand Action
Endpoint protection isn’t a back-office chore anymore, it’s a board-level KPI. Analysts peg worldwide endpoint security spend at US $27.46 billion for 2025, climbing at a 6.3 % CAGR. Meanwhile, Check Point logs a 44 % year-over-year surge in weekly cyber-attacks, confirming that threat actors are scaling faster than budgets. That pressure is forcing teams to embrace smarter defenses: 60 % of organizations already integrate AI into their security stack, with another 30 % actively evaluating it.
Key figures at a glance
- $27.46 B global endpoint security market in 2025
- 44 % spike in weekly cyber-attacks YoY
- 60 % of security teams using AI today
Endpoints now sit at the crossroads of identity, data and productivity, making them the easiest door to kick in and the last line of defense. As we unpack the five biggest trends shaping endpoint security 2025, note how solutions like Microsoft Endpoint Protection already align with this data-driven reality.
Trend #1 – AI-Powered Detection & Response Takes the Wheel
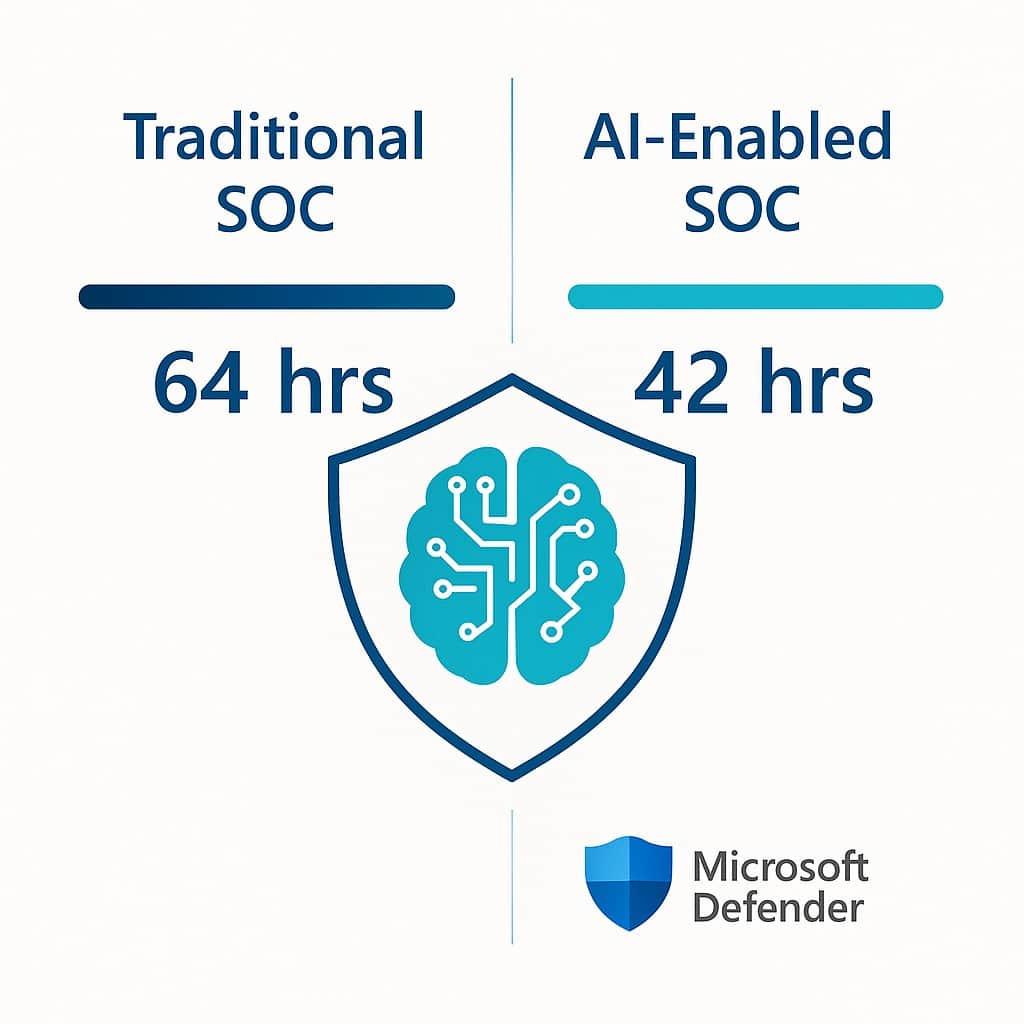
Security teams can’t hire analysts fast enough, so they’re letting algorithms shoulder the first wave of attacks. Gartner predicted that 80 % of Security Operations Centers would be using machine-learning-driven tools by 2024 and the momentum has only grown in 2025. IBM’s Cost of a Data Breach 2025 confirms the payoff: organizations with mature AI security shave ≈22 days off containment and save US $700 K per incident on average.
Why it matters in 2025
- Alert fatigue relief: AI triage slashes daily noise so human analysts focus on true positives.
- Faster decisions: Natural-language query and reasoning cut ‘search-and-stitch’ time during live incidents.
- Adaptive defenses: Models retrain constantly, recognizing novel ransomware TTPs in minutes.
Microsoft’s edge
- Microsoft Defender for Endpoint feeds trillions of signals into cloud ML to auto-isolate compromised devices and auto-reverse malicious changes.
- Microsoft Copilot for Security turns threat-hunter chat into KQL under the hood, surfacing root cause in plain English.
- Defender XDR scored 100 % detection coverage across every attack stage in the most recent MITRE ATT&CK® Enterprise evaluation.
Explore deeper: Microsoft Endpoint Protection | Defender for Office 365 vs Endpoint
Trend #2 – Identity-First Security & the March to Zero Trust
Identity is now every attacker’s favorite doorway and the numbers prove it:
These gaps explain why Zero Trust has become the North Star for endpoint protection: treat every access request as hostile until proven otherwise, continuously verify user and device health, and shrink the blast radius when (not if) credentials are stolen.
Why It Matters
- Credential theft remains the #1 breach vector. Attackers love endpoints because they hold cached tokens, saved passwords, and local admin rights.
- Shadow access is rampant. Nearly seven in ten ex-employees still have live credentials weeks after departure.
- Budget follows risk. Boards are green-lighting IAM, MFA, and Conditional Access projects faster than any other security line-item.
How Microsoft Closes the Identity Gap
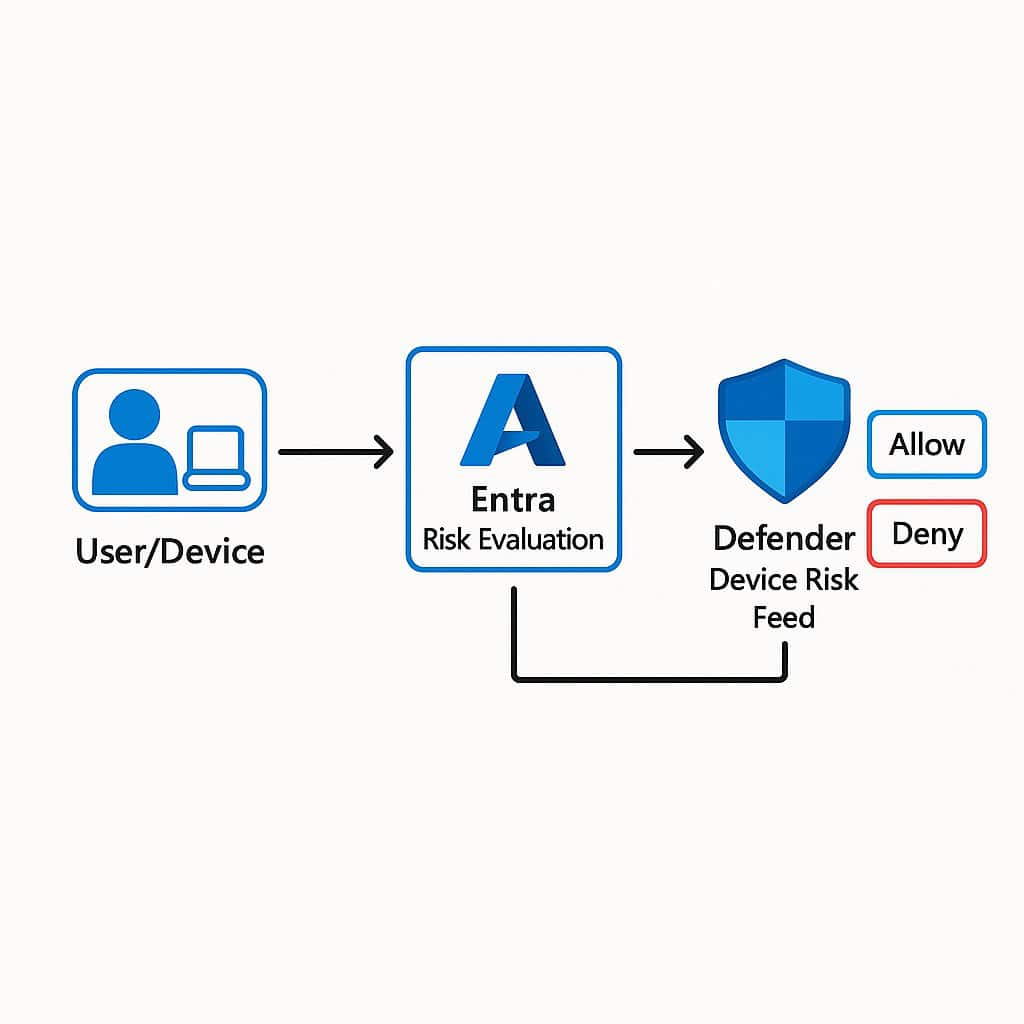
- Microsoft Entra ID + Conditional Access - assesses real-time risk (user location, sign-in behavior, device compliance) before granting tokens.
- Microsoft Defender for Endpoint - reports device risk back to Entra; non-compliant endpoints are quarantined automatically.
- Intune Device Health Attestation - validates TPM, Secure Boot, and OS integrity to enforce Zero Trust on every laptop and phone.
- Defender XDR incident queue - correlates identity signals with endpoint, email, and SaaS telemetry for one-click containment.
Trend #3 – XDR Everything: Consolidating Signals for Lightning-Fast Response
Security stacks have ballooned into a tangle of point tools enterprises now run ≈45 different security products on average, yet 53 % of teams say risk-reduction is still inadequate. The backlash is fueling an XDR (extended detection & response) gold-rush:
- XDR market projected to surge at a 20.3 % CAGR from 2025-2035 as organizations ditch siloed consoles for integrated, AI-powered platforms.
- Analysts note an XDR-as-a-Service boom and vendor consolidation aimed at taming complexity and shrinking mean-time-to-detect.
Why It Matters
- Fewer dashboards, faster decisions. Unified telemetry (endpoint + email + cloud + identity) collapses duplicate alerts into a single incident, trimming investigation times.
- Budget alignment. CISOs can rationalize licenses and prove ROI by linking detections to business impact.
How Microsoft Leads the XDR Wave
- Microsoft Defender XDR merges signals from Defender for Endpoint, Office 365, Entra ID, and more surfacing one correlated incident instead of dozens of individual alerts.
- Delivered 100 % detection coverage across every attack stage in the 2024 MITRE ATT&CK Enterprise evaluation.
- Automated attack disruption quarantines compromised devices and disables malicious tokens without analyst input.
- Tight Sentinel & Copilot for Security integration lets responders pivot from detection to hunt to remediation in the same pane of glass.
Trend #4 – Hardware Roots & Memory-Safe Code: Locking Hackers Out at the Silicon Layer
What’s changing
- The secure-boot & firmware-security market hits US $2.91 billion in 2025 as OEMs ship secured-core PCs by default and regulators push hardware roots of trust for critical infrastructure.
- Microsoft Pluton is now enabled on every Copilot+ PC announced for 2025, baking a Rust-based security processor into the CPU itself.
- Memory bugs still hurt: ≈70 % of Microsoft CVEs stem from memory-safety issues, and Google’s 2021 zero-day review found 75 % exploited the same class of flaws.
- In response, CISA & NSA formally urged all developers to adopt memory-safe languages in mid-2025.
Firmware + Memory Risk | Business Impact |
|---|---|
Stolen keys & bootkits bypass EDR entirely | Average recovery cost tops US $1.2 m per incident (IDC) |
Memory-safety exploits dominate in-the-wild zero-days | Patch cycles shrink but breach headlines grow |
Microsoft’s playbook
- Secure-core PCs & TPM 2.0 enforce measured boot, Credential Guard, and kernel isolation out-of-box no extra agents required.
Pluton stores secrets on-chip and receives Rust-based firmware updates directly from Microsoft.
Defender for Endpoint + Entra quarantine devices that fail hardware health attestation, blocking risky logins before they reach SaaS data.
Memory-safe momentum: Windows security components and the Pluton firmware itself are being rewritten in Rust to pre-empt entire exploit classes.
Trend #5 – Autonomous SOAR: Slashing Response Windows to Minutes
Security operations can only chase so many pings before fatigue wins hence the rush to security orchestration, automation & response (SOAR):
2025 Metric | Insight |
|---|---|
US $1.88 billion global SOAR market (up from $1.66 b in 2024; 13.6 % CAGR) | |
≈ 70 % faster incident response when AI-powered SOAR is enabled | |
Up to 85 % MTTR reduction in fully automated environments |
Why Communication Square Is Your Endpoint-Security Co-Pilot
When the headlines scream “44 % more cyber-attacks” and budgets balloon to US $27.46 billion , you need a partner that already lives in the trenches. Communication Square brings:
- Microsoft Solutions Partner - Security status with deep expertise across Defender, Entra, Intune, and Sentinel.
- 250 + secured tenants in government, education, healthcare, and SMB, protected by our 24 × 7 U.S.-based SOC.
- Fixed-fee, outcome-driven projects, no surprise invoices.
- Proven playbooks that unite Zero Trust, XDR, and SOAR on a single Microsoft cloud backbone.
- Hands-on enablement: from device baselines to user training, we stay until the last alert is green.
Success you can verify: See how we harden identities in Secure Microsoft Identity Protection and roll out end-to-end defenses in our Microsoft Endpoint Protection case studies.
Ready to Fortify Every Laptop, Phone & VM?
Download our free 2025 Endpoint Protection Checklist or jump straight to action: Book a 30-minute Cloud-Strategy Call →. We’ll map your device inventory against the five trends you’ve just read and show you how Microsoft Defender and friends can start reducing risk this quarter.
Last Updated 6 months ago ago
