Understanding Azure Information Protection
Welcome to the third part of our blog series on Microsoft 365 for Enterprise Security. In the first two parts, we covered the importance of Identity and Access Management and Threat Protection in securing sensitive data in today's digital landscape. In this post, we will delve into the world of Azure Information Protection and explore the various tools and strategies that can be used to safeguard digital assets against unauthorized access and misuse.
Discover the topic at hand through our engaging video, or if you're more of a reader, we've also got a detailed blog post available. So, whether you prefer to watch or read, we've got you covered!
Protecting sensitive and highly regulated digital assets is a crucial component of any effective security program. Organizations must have a clear understanding of the risks involved and the best practices for protecting their information from cyber threats, accidental leaks, and unauthorized access. The following sections will provide an overview of the various tools and strategies that can be used to safeguard digital assets against such threats using Microsoft Information Protection tools.
Protect Sensitive and Highly Regulated Digital Assets with Azure Information Protection Labels.
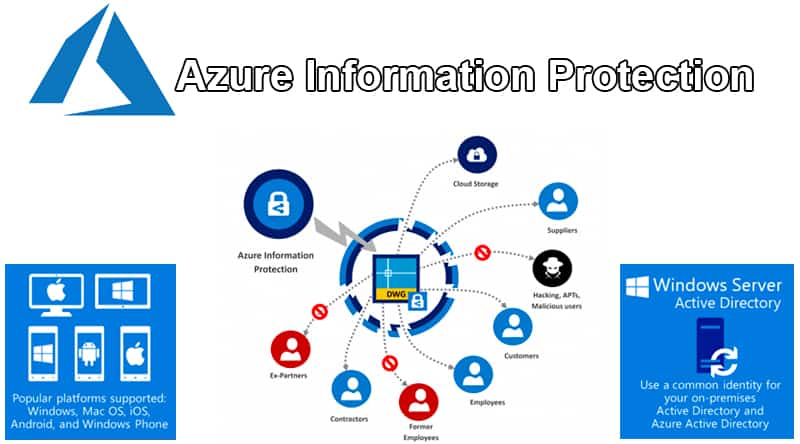
What is Azure Information Protection (AIP)?
Azure Information Protection is a cloud-based solution that enables enterprises to classify, label, and protect their sensitive data. With AIP, enterprises can apply labels to their documents and emails, which helps to identify and classify sensitive data. These labels provide protection to the data by encrypting it and setting up access policies that limit who can access it. AIP provides a comprehensive set of labels that can be customized based on the enterprise's requirements. The labels can be applied automatically or manually, and they are visible across all platforms and devices.
Benefits of Using Azure Information Protection Labelling to Protect Sensitive Data
Some of the key benefits of using Azure Labelling to protect sensitive data include:
- Improved data security: AIP labels help to protect sensitive data from unauthorized access, both internally and externally.
- Compliance with regulations: AIP labels help enterprises to comply with industry and government regulations related to data protection and privacy.
- Better data management: AIP labels help to identify and classify data, which makes it easier to manage and organize sensitive data.
AIP labels can be useful in a wide range of scenarios, such as protecting financial data, intellectual property, Personally Identifiable Information (PII), and more. Read our case study on Azure Information Protection Solution for Healthcare.
Prevent Intranet Data Leaks with Microsoft Purview Data Loss Prevention (DLP)
Before we dive in further, let’s find out what Data Loss Prevention is. Data Loss Prevention (DLP) is a feature of Microsoft 365 that helps enterprises to prevent the leakage of sensitive data. DLP policies enable enterprises to identify and prevent the unauthorized sharing of sensitive data within the enterprise's intranet. Azure Data Loss Prevention policies can be customized to meet the enterprise's specific requirements, and they can be applied to a wide range of data types, including email, documents, and SharePoint sites.
Some of the key benefits of using Office 365 Data Loss Prevention solutions to prevent data leaks include:
- Prevent data breaches: DLP policies can help to prevent data breaches by detecting and preventing the unauthorized sharing of sensitive data.
- Improved compliance: DLP policies help enterprises to comply with industry and government regulations related to data protection and privacy.
- Better data management: DLP policies help to identify and classify data, which makes it easier to manage and organize sensitive data.
Prevent Device Data Leaks with Microsoft Purview Information Protection
Microsoft Purview Information Protection (formerly known as Microsoft Information Protection) is a tool designed to help organizations prevent data leaks by allowing them to manage and protect sensitive information stored in their devices. The tool leverages Microsoft's machine learning and artificial intelligence capabilities to scan and classify data based on its sensitivity level, enabling organizations to implement appropriate policies and controls to ensure that the data is secure.
Microsoft Purview Information Protection also offers features that allow organizations to easily identify and locate sensitive data across their devices, including cloud-based applications and services. The tool provides a unified dashboard where administrators can view and manage data access policies and settings, enabling them to quickly respond to potential data leaks or security incidents.
Furthermore, Microsoft Purview Information Protection integrates with other Microsoft tools, including Azure Information Protection and Microsoft 365 Compliance, enabling organizations to easily extend their data protection policies and controls across different platforms and applications. This integration also allows organizations to automate certain processes, such as classifying data and applying appropriate labels and access policies.
Overall, Microsoft Purview Information Protection is a valuable tool for organizations looking to enhance their data protection strategies and prevent data leaks across their devices and cloud-based applications. By leveraging Microsoft's advanced technologies and integrations, organizations can quickly and easily identify and protect sensitive data, while also implementing policies and controls to ensure that the data remains secure.
Why did Microsoft discontinue Windows Information Protection (WIP)?
Windows Information Protection, formerly known as Enterprise Data Protection (EDP), was initially created to assist businesses in safeguarding their apps and data from unintentional data breaches without disrupting the user experience on Windows. However, many organizations have voiced their need for a data protection solution that can work across different platforms and extend sensitive data protection controls to endpoints for various SaaS apps and services. To meet these requirements, Microsoft developed Microsoft Purview Data Loss Prevention (DLP), which works closely with Microsoft Purview Information Protection to enable organizations to discover, classify, and protect sensitive data as it is used or shared.
While Windows Information Protection can prevent accidental data leaks from well-intentioned employees, it is not intended to prevent malicious insiders from stealing enterprise data and protect enterprise privacy protection. WIP will continue to be maintained by Microsoft on supported versions of Windows. WIP will not be included in new versions of Windows, and it will not be supported in future versions of Windows.
As increased organizations adopt cloud-based services for their operations, it's becoming increasingly important to have effective cloud security measures in place. Microsoft Defender for Cloud Apps is a powerful cloud security tool that enables organizations to monitor and protect their cloud-based assets.
Last Updated 1 year ago
