Introduction to Threat Protection
In this second part of our blog series "Microsoft 365 for Enterprise Security," we will focus on Microsoft advanced threat protection. As a continuation of our previous blog posts "Part 1 - Identity and Access Management” where we discussed the importance of securing digital identities, protecting against cyber threats and malware, and monitoring cloud applications, we will now shift our focus to the importance of Threat Protection and the various security measures that can be implemented to protect sensitive data and systems from attacks.
Microsoft advanced threat protection is critical for maintaining the security of an organization's data and digital assets. Cyber-attacks and data breaches can result in serious consequences for businesses, including financial loss, damage to reputation, and loss of customer trust. Threat protection involves implementing security measures to prevent, detect, and respond to security incidents, including malware attacks, phishing attacks, and other types of cyber threats.
In this blog post, we will provide an overview of the various threat protection measures that can be implemented using Microsoft 365. Specifically, we will discuss the best Threat Protection software's, including how Microsoft Defender Antivirus, Microsoft Defender for Office 365, Office 365 Threat Investigation and Response, and Advanced Threat Analytics can be used to protect an organization's digital assets from cyber threats and attacks.
If you're short on time or prefer a more visual approach, we've got you covered with a comprehensive YouTube video on the topic. However, if you're someone who enjoys a more in-depth read, we've got you covered with our blog post.
Protection from Malware with Microsoft Defender Antivirus
Malware is one of the most common and harmful types of cyber threats that can affect an organization's data security. Malware can include viruses, trojans, worms, spyware, and other malicious software that can infect a computer or a network and cause damage or steal sensitive data. That's why it is crucial to have effective malware protection in place. The following table compares the features of Microsoft Defender Antivirus vs Microsoft Defender for Endpoint Antivirus.
Features | Microsoft Defender Antivirus | Microsoft Defender for Endpoint |
|---|---|---|
Threat detection and prevention | Yes | Yes |
Endpoint protection | No | Yes |
Network protection | No | Yes |
Automated investigation and remediation | No | Yes |
Behavior-based detection | Yes | Yes |
Machine learning-based detection | Yes | Yes |
Real-time protection | Yes | Yes |
Cloud-powered protection | Yes | Yes |
Endpoint detection and response (EDR) | No | Yes |
Advanced hunting and investigation | No | Yes |
Microsoft Defender Antivirus for Malware Protection and Management on Windows 11 Enterprise Devices
Microsoft Defender Antivirus is a built-in feature in Windows 11 Enterprise that provides malware protection and anti-malware management for PCs and devices running on the Windows operating system. It uses real-time protection, cloud-delivered protection, and behavior-based detection to protect devices from malware threats.
Real-time protection constantly monitors the system for malware activity and provides alerts and actions to take against it. Cloud-delivered protection uses the Microsoft Defender Antivirus cloud service to help protect devices against new and emerging threats. Behavior-based detection identifies and blocks suspicious behavior of programs and files that could indicate malware activity.
Benefits of Using Microsoft Defender Antivirus for Malware Protection
So, is Microsoft Defender any good? Some of the key benefits of using Microsoft Defender Antivirus for malware protection include:
- Comprehensive protection: Microsoft Defender Antivirus offers a wide range of protection options that cover several types of malware threats.
- Automatic updates: The software is constantly updated with the latest Office 365 threat intelligence, which ensures that the devices are always protected against new and emerging threats.
- Integration with Microsoft 365: Microsoft Defender for Office 365 is tightly integrated with other Microsoft 365 security tools, such as Microsoft Defender for Office 365 and Azure Office 365 Advanced Threat Protection, to provide a comprehensive security solution for enterprise environments.
- Easy management: Microsoft Defender Antivirus can be easily managed and configured through the Microsoft Endpoint Manager console, making it simple to deploy and maintain across the enterprise.
Examples of Scenarios where Microsoft Defender Antivirus is Useful
Some examples of scenarios where Microsoft Defender Antivirus is useful include:
- Preventing malware infections: Microsoft Defender Antivirus can detect and prevent malware infections before they cause harm to devices or data.
- Reducing IT costs: As a built-in feature of Windows 11 Enterprise, Microsoft Defender Antivirus eliminates the need for additional third-party antivirus software, reducing IT costs and simplifying device management.
- Securing remote devices: With the increase in remote work, protecting devices from malware threats is more important than ever. Microsoft Defender Antivirus provides protection to devices, whether they are on-premises or remote, ensuring that the devices and the data are always safe.
Comparing Microsoft Defender Antivirus to other antivirus software
Antivirus Software | Platform | Cost | Malware Detection Rate | False Positive Rate | System Performance Impact | Additional Features |
|
|---|---|---|---|---|---|---|---|
Microsoft Defender Antivirus | Windows | Included with Windows 11 | High | Low | Minimal | Cloud-based protection, built-in to Windows 11 here... | You can add up to 4 additional devices (for a total of 5 per person) |
Norton 360 | Windows, MacOS | $99.99/year | High | Low | Medium | Dark web monitoring, parental controls | 10 devices |
McAfee Total Protection | Windows, MacOS, iOS, Android | $119.99/year | High | Medium | High | VPN, identity theft protection, password manager | 5 devices |
Kaspersky Total Security | Windows, MacOS, iOS, Android | $65.99/year | High | Low | Medium | VPN, password manager, parental controls | 5 user accounts/ 10 devices |
Avast Premium Security | Windows, MacOS, iOS, Android | $99.99/year | Medium-High | Low | High | VPN, password manager, firewall | 10 devices |
In the next section, we will discuss how Microsoft Defender for Office 365 provides secure email flow and mailbox audit logging.
Secure Email Flow and Mailbox Audit Logging with Microsoft Defender for Office 365
Email remains one of the most important communication tools for businesses. With so much sensitive information being transmitted through email, it is essential to ensure that email security is a top priority. Microsoft provides powerful tools to protect against email-borne threats and to help secure email flow and mailbox audit logging. In this blog post, we will discuss how Exchange Online Protection and Defender for Office 365 can be used for secure email flow and mailbox audit logging and provide some examples of scenarios where these tools are useful.Exchange Online Protection vs Microsoft Defender for Office 365
Exchange Online Protection (EOP) is a cloud-based email filtering service that protects your organization against spam and malware. EOP is included in Microsoft 365 subscriptions and works in conjunction with microsoft advanced threat protection to provide a comprehensive email protection solution. Defender for Office 365 provides additional protection against unknown malware, viruses, and malicious URLs transmitted through emails. It is a cloud-based email filtering service that uses machine learning to protect against email-based attacks, including phishing and impersonation attempts.
Features | Exchange Online Protection | Defender for Office 365 |
|---|---|---|
Anti-spam filtering | Yes | Yes |
Anti-malware filtering | Yes | Yes |
URL protection | No | Yes |
Phishing protection | No | Yes |
Anti-spoofing | No | Yes |
Anti-phishing | No | Yes |
Automated investigation | No | Yes |
Reporting and tracking | Yes | Yes |
Custom policies | Yes | Yes |
Custom rules | Yes | Yes |
Benefits of Secure Email Flow and Mailbox Audit Logging Tools
One of the key benefits of using Exchange Online Protection and Defender for Office 365 is that they provide a layered approach to email security. EOP provides basic protection against spam and malware, while Defender for Office 365 provides advanced protection against more sophisticated threats. By using these tools in combination, you can create a comprehensive email security solution that helps protect your organization from a wide range of threats.
Real-world Applications of These Tools: Bringing Security to Life
There are many scenarios where EOP and Defender for Office 365 can be useful. For example, if your organization has a high volume of email traffic, it can be difficult to manually monitor for spam and malware. EOP and Defender for Office 365 can help automate this process and provide real-time protection against email-based threats. Additionally, if your organization is subject to compliance regulations, mailbox audit logging can help ensure that you are meeting your regulatory requirements.
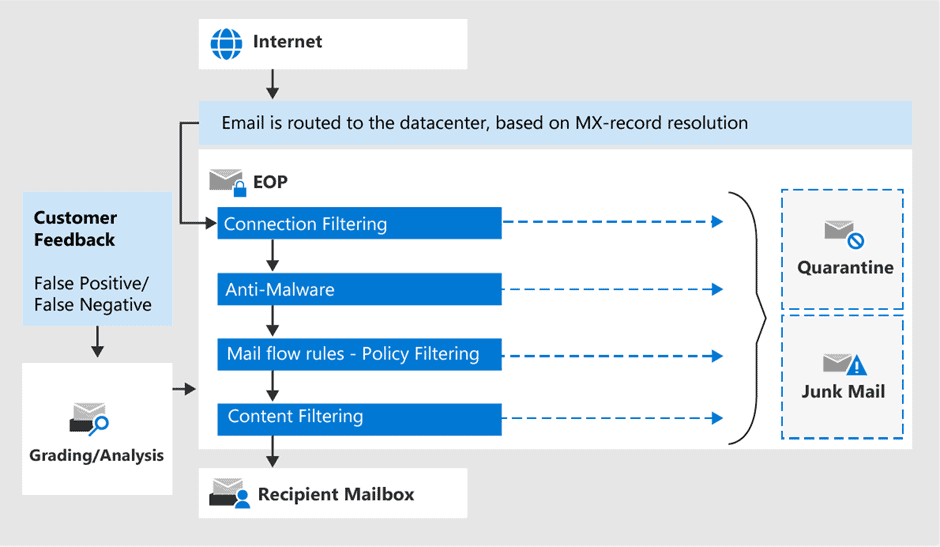
Defending Against Top 10 Email Threats with Microsoft Defender for Office 365
In the following table, we will look at the top 10 email-based threats and how Microsoft Defender for Office 365 helps protect against them.
Item 1 | Item 2 | Item 3 |
|---|---|---|
Phishing | Emails designed to trick users into revealing sensitive information or downloading malware | Anti-phishing protection, URL detonation |
Spear Phishing | Targeted phishing attacks against specific individuals or organizations | Anti-phishing protection, URL detonation, detonation of attachments |
Spoofing | Emails designed to impersonate a trusted sender or organization | Anti-spoofing protection, DMARC verification |
Malware | Emails with malicious attachments or links | Malware protection, attachment detonation, URL detonation |
Ransomware | Malware that encrypts user files and demands payment for decryption | Ransomware protection, behavior monitoring |
Business Email Compromise (BEC) | Emails designed to impersonate an executive or vendor in order to conduct fraud or steal money | Anti-spoofing protection, DMARC verification, URL detonation |
Advanced Threats | Sophisticated attacks designed to evade traditional security measures | ATP safe attachments, ATP safe links, detonation of attachments |
Zero-day attacks | Attacks exploiting vulnerabilities that are unknown to the software vendor | Behavior monitoring, exploit protection |
Spam | Unsolicited emails, often containing unwanted content or scams | Anti-spam protection |
Graymail | Emails that are not spam but are not important to the user, such as newsletters and marketing emails | Advanced filtering, prioritization of important emails |
In summary, EOP and Defender for Office 365 provide a powerful set of tools for securing email flow and mailbox audit logging. By using these tools in combination, organizations can create a comprehensive email security solution that helps protect against a wide range of threats. Whether you are looking to protect against spam and malware, or you need to meet regulatory requirements, EOP and Defender for Office 365 can provide the protection and monitoring capabilities you need.
Microsoft advanced threat protection and Response for Advanced Attack Monitoring and Prevention
Cyber-attacks are becoming increasingly common. Attackers are continually looking for ways to steal sensitive data or disrupt business operations. Office 365 threat investigation and response is a tool that can help organizations detect and respond to these attacks.
Office 365 threat investigation and response is a cloud-based service that provides a central location for managing threat intelligence and conducting investigations. It allows organizations to identify and respond to attacks in real-time. The tool integrates with other Microsoft security products and services, such as Microsoft Defender for Endpoint, to provide a complete security solution.
Using Office 365 threat investigation and response, organizations can monitor their environment for suspicious activities, such as anomalous logins, data exfiltration attempts, and phishing emails. The tool analyzes this information and provides insights into the scope of the attack and the potential impact on the organization.
Protection from Sophisticated Attacks with Advanced Threat Analytics
Advanced Threat Analytics (ATA) is a security solution that uses machine learning to detect and prevent advanced targeted attacks. ATA is designed to provide real-time visibility into identity, device, and resource activity in a network, so that security teams can quickly identify and respond to potential threats.
ATA works by analyzing normal and abnormal user and device behavior to identify potential threats. It creates a baseline of what is normal on the network and alerts security teams when an activity is detected that deviates from this baseline. This proactive approach allows security teams to detect and prevent attacks before they cause severe damage.
Defending Your Enterprise Against Advanced Attacks: The Benefits of Microsoft Advanced Threat Analytics
One of the key benefits of using ATA is its ability to detect threats that traditional security solutions may miss. ATA is designed to detect threats that use stolen credentials, insider threat protection, and other advanced tactics. By detecting these types of threats, ATA can help prevent data breaches and other types of cyberattacks.Another benefit of ATA is its ease of use. It is designed to integrate with existing security solutions, making it easy for security teams to implement and manage. It also provides a simple dashboard that displays all the detected threats and allows security teams to investigate and respond to them quickly.
Examples of Scenarios Where Advanced Threat Analytics is Useful
Examples of scenarios where ATA is useful include detecting unusual behavior by a privileged user, identifying suspicious activity on a sensitive file share, and detecting attempts to steal data by an external attacker. In each of these scenarios, ATA can help prevent data breaches and other types of cyberattacks by detecting and responding to threats in real-time.
Attack Scenario | Description | How ATA can prevent or mitigate |
|---|---|---|
Spear-phishing attacks | Emails with malicious links or attachments sent to specific individuals | ATA can detect and alert on abnormal authentication and authorization behavior, such as a user logging in from an unknown location or using suspicious credentials. |
Password spraying | Attackers try a few commonly used passwords across many user accounts | ATA can detect and alert on brute-force attacks and repeated failed login attempts, and can trigger automatic account lockout or password reset. |
Pass-the-hash | Attackers steal password hashes and reuse them to access other systems | ATA can detect and alert on attempts to use stolen credentials, even if the attacker does not know the actual password. |
Golden ticket attacks | Attackers create forged Kerberos tickets to gain unrestricted access to a domain | ATA can detect and alert on anomalies in the Kerberos authentication process, such as ticket-granting ticket (TGT) requests from unusual sources or with unusual lifetimes. |
Domain trust exploitation | Attackers compromise a trusted domain to gain access to another domain | ATA can detect and alert on suspicious cross-domain authentication behavior, such as a user from one domain accessing resources in another domain without a valid reason. |
Remote execution attacks | Attackers use remote code execution to take control of a system | ATA can detect and alert on attempts to use remote execution tools or techniques, such as PowerShell, PsExec, WMI, or SMB. |
Malware attacks | Attackers use malicious software to steal data or cause damage | ATA can detect and alert on suspicious file and process activity, including attempts to execute known malware or create new files with unusual extensions. |
DNS tunneling | Attackers use DNS queries and responses to communicate with a command and control server | ATA can detect and alert on unusual DNS traffic patterns, such as large DNS requests, long response times, or unusual domain names. |
SQL injection attacks | Attackers use SQL queries to exploit vulnerabilities in a web application | ATA can detect and alert on attempts to inject malicious SQL code, or on unusual SQL traffic patterns, such as repeated requests for non-existent tables. |
Zero-day attacks | Attackers use previously unknown vulnerabilities to gain access or control | ATA can detect and alert on abnormal behavior patterns that could indicate a new or unknown threat, such as a user accessing a resource that they have never accessed before, or an unusual sequence of events. |
Implementing Microsoft Advanced Threat Protection in Your Organization
In conclusion, effective threat protection is a critical component of any organization's security strategy. The Microsoft 365 suite provides several tools that can help protect your organization from a wide range of cyber threats. In this blog post, we discussed some of the key aspects of Advanced Threat Protection Microsoft 365, including protection from malware with Microsoft Defender Antivirus, secure email flow and mailbox audit logging with Microsoft Defender for Office 365, attack monitoring and prevention with Office 365 threat investigation and response, and protection from sophisticated attacks with Advanced Threat Analytics.
As part of our Microsoft 365 for Enterprise Security series, we have also covered Identity and Access Management in Part 1, Information Protection in Part 3, and Security Management in Part 4. By implementing these solutions, you can help safeguard your organization against a wide range of threats, from identity theft to cyber-attacks.
At Communication Square, we are a leading provider of Microsoft 365 security solutions. We specialize in helping organizations of all sizes implement and manage these solutions to protect their critical assets and data. Contact us today to learn more about how we can help you implement a comprehensive Microsoft 365 security strategy.
Last Updated 1 month ago


