Background on Phishing
Phishing is a type of cyberattack that involves tricking individuals into revealing sensitive information such as passwords, credit card numbers, and other personal information. The attacker impersonates a trustworthy entity, such as a bank or a government agency, to gain the victim's trust and trick them into divulging confidential information.
Don't have the time to read a lengthy blog post? No problem! Check out our latest video on the topic at hand, or if you prefer to read, we've got a comprehensive blog post waiting for you to dive into.
Phishing attacks can be launched in a variety of ways, including email, social media, phone calls, malicious software, and instant messaging. In most cases, phishing attacks are launched through email. The attacker will send an email that appears to be from a reputable source, such as a bank or a well-known company, and ask the recipient to click on a link or open an attachment. The link or attachment will then redirect the victim to a fake website that looks identical to the legitimate one.
For instance, there are numerous phishing attack examples where attackers use fake websites to steal login credentials.
It is crucial to understand phishing and the different tactics that attackers use to gain access to sensitive information. With the increasing use of technology, phishing attacks are becoming more sophisticated, making it even more important for individuals and companies to take the necessary steps to protect themselves.
To prevent phishing attacks and protect sensitive information, it is essential to be aware of phishing attack countermeasures and the tactics used by attackers. Studying various phishing attack examples can provide valuable insights into these tactics. It is also important to educate employees on how to recognize and avoid phishing attempts, and to implement technical measures such as spam filters and two-factor authentication.
The Impact of Phishing on Companies
Phishing attacks are having a major impact on companies, causing significant financial losses, reputational damage, and productivity losses.
A. Financial Losses
1. Loss of sensitive data
Phishing attacks often result in the theft of sensitive information such as confidential business information, customer data, and intellectual property. This can have a significant financial impact on a company, as it may lead to lawsuits, fines, and a loss of business.
2. Loss of money from cyberattacks:
In addition to the theft of sensitive information, phishing attacks can also result in the direct loss of money from cyberattacks such as wire transfer fraud or ransomware attacks
For example, some phishing attack examples involve convincing employees to wire money to fraudulent accounts.
B. Reputational Damage
1. Loss of customer trust:
Companies that fall victim to phishing attacks risk losing the trust of their customers. The loss of sensitive information, such as personal and financial data, can erode customer trust and have a lasting impact on a company's reputation.
2. Negative publicity:
In addition to damaging customer trust, phishing attacks can also result in negative publicity, which can further damage a company's reputation and negatively impact business.
C. Productivity Losses
1. Loss of customer trust:
Companies that fall victim to phishing attacks risk losing the trust of their customers. The loss of sensitive information, such as personal and financial data, can erode customer trust and have a lasting impact on a company's reputation.
2. Negative publicity:
In addition to damaging customer trust, phishing attacks can also result in negative publicity, which can further damage a company's reputation and negatively impact business.
The impact of phishing attacks on companies can be significant and far-reaching. It is essential for companies to take the necessary steps to prevent phishing attacks and protect sensitive information.
Common Phishing Techniques
Phishing attacks can take many forms, and attackers are constantly developing new tactics to trick individuals into revealing sensitive information. Some of the most common phishing techniques include:
A. Email Phishing
1. Spoofed emails:
In fake email phishing, attackers send emails that are from a trustworthy source, such as a bank or a well-known company. The emails contain a link or an attachment that, when clicked, redirects the victim to a fake website that looks identical to the legitimate one.
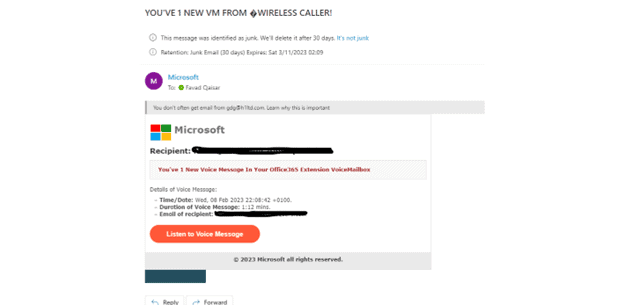
2. Email attachments:
Another common technique in email phishing frauds is to send an email that contains an attachment, such as a PDF or a Microsoft Office document, which contains malicious code. When the attachment is opened, the attacker gains access to the victim's computer and sensitive information.
B. Website Phishing
1. Fake websites
In website phishing, attackers create fake websites that look identical to the legitimate ones, to trick victims into entering sensitive information. This can include sites for banks, government agencies, and well-known companies.
2. Social Engineering
In social engineering, attackers use psychological manipulation to trick individuals into revealing sensitive information. This can include creating fake profiles on social media, posing as a customer service representative, or using scare tactics to get the victim to divulge sensitive information.
C. Telephone Phishing
1. Vishing (Voice Phishing)
In vishing, attackers use voice calls to trick individuals into revealing sensitive information. This can include impersonating a bank or government agency and asking the victim to provide personal information over the phone.
2. Smishing (SMS Phishing)
In smishing, attackers send text messages that don't look like suspicious messages to trick individuals into revealing sensitive information. The text messages often contain a link that, when clicked, redirects the victim to a fake website that looks identical to the legitimate one.
Reviewing various phishing attack examples, such as those involving fake calls or fraudulent SMS messages, can help individuals and companies better understand and recognize these tactics.
It is important to understand these common phishing techniques and to educate employees on how to recognize and avoid phishing attempts. This can help prevent phishing attacks and protect sensitive information.
How Can You Spot the Scam?
Make no mistake, these attacks can be cunning. These types of phishing exist because they work. Scammers launch thousands of phishing campaigns and they’re often successful. The FBI’s Internet Crime Complaint Center reported that people lost $57 million to phishing schemes in one year. Here are a few pointers for you to identify an email that is a fraud using phishing emails:
- The email is never addressed to the recipient. If the recipient is truly being reached out to, they would know the recipient’s name. "Dear Customer" isn’t an identifier.
- Grammatical errors: Words capitalized without proper grammatical use or too much punctuation is also a factor but since most people scan emails quickly, grammatical errors that are this small usually don’t get noticed in the browser window.
- They try to reassure recipients by encouraging them to confirm the email is from who they’re posing as by providing a link of some sort in the email.
- The emails may say they’ve noticed some suspicious activity or log-in attempts.
- Emails might claim there’s a problem with your account or your payment information.
- They may say you must confirm personal information.
- They can easily include a fake invoice.
- These emails would want you to click on a link to make a payment.
- Suggest you’re eligible to register for a government refund or offer a coupon for free stuff.
Seeing any one of these flaws is enough to tell you the email is a phishing attempt – but what if these errors aren’t there at all?
A smarter fraudster could have corrected these mistakes, including knowing the recipient’s name and email address and masking their URL in a much more convincing way. If they'd done a better job, there would have been nothing alarming in the message. But it would still be a fake. Exploring various phishing attack examples can show how sophisticated these scams can get, making it even more important to stay vigilant.

Prevention and Mitigation
There are several steps companies can take to protect themselves from phishing attacks and minimize the impact of a successful attack.
A. Employee Awareness and Training
1. Regular training sessions
Regular training for employees is essential to prevent phishing attacks. Employees should be trained in phishing email prevention, to avoid clicking on suspicious links or attachments, and to understand the importance of not revealing sensitive information. Employees should also be provided with extensive training regarding best practices for phishing emails, examples of fraud emails, and what types of information fraudsters target.
2. Phishing simulation exercises
Companies can also conduct simulated phishing attacks to test employees' awareness and understanding of phishing tactics. This can help to identify employees who may be more susceptible to phishing attacks and provide targeted training to improve their awareness and understanding.
B. Technical Measures
1. Spam filters
Implementing spam filters can help to prevent phishing e mails from reaching employees' inboxes. Spam filters can be configured to block emails that contain certain keywords or that come from suspicious sources.
2. Two-Factor Authentication
Implementing spam filters can help to prevent phishing emails from reaching employees' inboxes. Spam filters can be configured to block emails that contain certain keywords or that come from suspicious sources.
3. Encryption
Encrypting sensitive information can help to prevent unauthorized access if a phishing attack is successful. Encryption is the process of converting data into a code that only authorized users can access.
C. Prevent Phishing Attacks with Microsoft Cloud Solutions
Microsoft provides a comprehensive suite of cloud-based solutions to help companies protect against phishing attacks and other cyber threats. These solutions are designed to provide advanced security features that can help to prevent and mitigate the impact of a successful attack.

1. Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is a cloud-based endpoint security solution designed to provide comprehensive protection against phishing attacks and other cyber threats. This solution includes antivirus protection, firewall protection, and behavioral analysis, which can detect and prevent phishing attacks in real-time. Microsoft Defender for Endpoint helps to secure endpoint devices whether they are using mobile device management such as computers, laptops, and mobile devices, ensuring that sensitive information is protected from phishing attacks and other cyber threats.
2. Azure Advanced Threat Protection
Microsoft 365 is a comprehensive suite of productivity and collaboration tools that includes advanced security features to help protect against phishing attacks. With Advanced Threat Protection, Microsoft 365 uses machine learning algorithms to detect and block phishing emails, keeping sensitive information safe. Multi-factor authentication is also available, adding an extra layer of security to prevent unauthorized access to sensitive information, even if a phishing attack is successful.
By using Microsoft's cloud-based solutions, companies can benefit from advanced security features that can help to prevent and mitigate the impact of phishing attacks. These solutions provide a proactive approach to security, helping to ensure the protection of sensitive information and the continued success of the business.
D. Response and Recovery
In the event of a successful phishing attack, it's essential to have a plan in place for responding and recovering from the incident. This includes identifying the scope of the attack, containing the damage, and implementing measures to prevent future attacks.
- Incident Response Plan: A well-defined incident response plan is critical in responding to a phishing attack. This plan should outline the steps that need to be taken, including who to contact, what to do, and when to do it. Having a plan in place can help to minimize the impact of a phishing attack and ensure a quick and effective response.
- Containment and Eradication: Once the phishing attack has been identified, the first step is to contain and eradicate the threat. This may involve disabling the infected systems, disconnecting from the network, and cleaning up the malware.
- Data Backup: Regularly backing up important data is crucial in ensuring that the company can recover from a phishing attack. In the event of an attack, data backups can be used to restore systems and data to their previous state.
- User Education: User education is essential in preventing future phishing attacks. Employees should be trained in how to recognize phishing attempts and how to respond if they receive a suspicious email. Regular training and reminders can help to keep employees aware of the latest phishing techniques and prevent future attacks.
By having a response and recovery plan in place, companies can minimize the impact of a phishing attack and ensure a quick and effective response. Implementing these measures can help to prevent future attacks and ensure the continued success of the business.
Conclusion and Recommendations
A. Recap of the Impact of Phishing
Phishing attacks continue to be a significant threat to companies, causing widespread damage and financial losses. It's essential for companies to understand the risks and take steps to protect against these attacks. Implementing a comprehensive security strategy, including advanced security features from Microsoft cloud solutions and regular user education, can help to prevent and mitigate the impact of phishing attacks.
B. The Importance of Staying Vigilant
For those who are looking for a trusted and experienced partner to help secure their data from potential phishing attacks, Communication Square can be a valuable resource. Communication Square is a Microsoft award-winning Gold Partner with expertise in Microsoft cloud solutions and security. They can help assess your current security score and provide tailored solutions to secure your data and systems from potential phishing attacks. They can also offer guidance on identifying phishing attacks, such as teaching employees how to recognize the warning signs of a phishing email and asking, "is this email phishing?" before taking any actions based on the email.
C. Final Thoughts and Recommendations
In conclusion, phishing attacks are a growing threat to companies and require a proactive approach to security. By implementing advanced security features and regular user education, companies can protect against these attacks and ensure the continued success of the business. Partnering with a trusted and experienced provider, like Communication Square, can provide additional peace of mind and support in securing your data from potential phishing attacks.
Last Updated 1 year ago
