In this final part of our series "Microsoft 365 for Enterprise Security," we will focus on Security Management. As we discussed in previous blog posts, effective security management is critical to protecting your organization from cyber threats. In the ever-evolving landscape of enterprise security, managing threats and ensuring data protection can be challenging. For many businesses, partnering with a managed security service provider can offer significant advantages in navigating these complexities. Microsoft 365 for Enterprise delivers a comprehensive suite of security management tools designed to protect your organization against sophisticated threats and maintain regulatory compliance.
In this blog post, we will cover best practices for security management, including the importance of a Central Security Dashboard for IT and users.
Importance of a Central Security Dashboard for IT and Users
A Central Security Dashboard provides a single pane of glass view of your organization's security status, allowing you to quickly identify and respond to security threats. This dashboard is a key component of effective security management and can help your IT team to manage security more easily across your organization.
Whether you prefer to watch a video or dive deep into a blog post, we've got you covered! Our latest video covers the topic at hand in detail, and we also have this comprehensive blog post available for those who prefer to read.
We will also cover Microsoft Defender for Cloud and Windows Defender Security Center, two powerful tools that can help you to implement a Central Security Dashboard. These tools provide a range of features that can help you to monitor and manage security across your organization, including threat analytics, device management, and vulnerability assessment.
By implementing a central security dashboard with Microsoft Defender for Cloud and Windows Defender Security Center, you can streamline your security management and better protect your organization from cyber threats.
Microsoft Defender for Cloud
Microsoft Defender for Cloud is a cloud-native security solution that provides unified visibility and control over hybrid workloads, including virtual machines, servers, containers, and apps. It is designed to deliver integrated and automated security to protect workloads across multiple clouds and platforms.
Do you know? 43% of breaches take place at small business
Go Passwordless! The future is here for your Microsoft account, and it no longer requires a password! No more worrying about a breach happening to your business. This Free Inforgraphic will list everything that is potentially at risk and how to protect it.
Benefits of Microsoft Defender for Cloud
One of the key benefits of Microsoft Defender for Cloud is its Central IT Security Dashboard. This dashboard offers visibility into security alerts and incidents, as well as access to security recommendations and best practices. With this centralized view, IT teams can quickly and efficiently respond to threats, reducing the risk of a security breach.
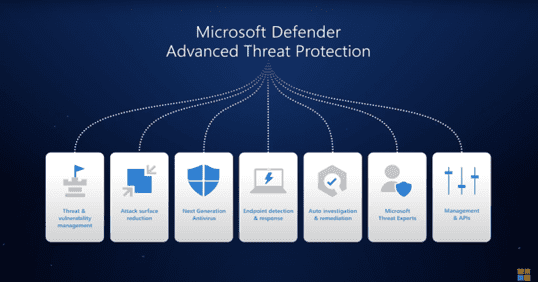
Features of Microsoft Defender for Cloud's Central Security Dashboard
In addition to its Central Security Dashboard, Microsoft Defender for Cloud offers several features to help organizations manage security across their hybrid workloads. These features include endpoint detection and response, threat and vulnerability management, and cloud security posture management. Together, these tools provide comprehensive security management capabilities that can help organizations protect against a wide range of threats.
Security Event | Microsoft Defender for Cloud Feature |
|---|---|
Malware attack | Real-time detection and remediation of malware with automated investigation |
Automatic remediation of ransomware infections and prevention of propagation | |
Phishing attempts | Multi-layered anti-phishing protection including Safe Links and Safe Attachments |
Data leakage or exfiltration | Data Loss Prevention (DLP) policies and sensitivity labels with real-time monitoring |
Account compromise | Automated investigation and remediation with conditional access and Multi-factor Authentication |
Insider threat detection | Behavioral analytics and machine learning to detect anomalous user activity |
Suspicious logins | Automated investigation with risk-based conditional access and MFA |
Rogue devices on network | Network and device security assessments with continuous monitoring and threat alerts |
Malicious IP or domain access | Threat intelligence and IP reputation tracking with automatic blocking and alerting |
Unauthorized app installations | App protection policies with real-time monitoring and control |
Windows Defender Security Center
Overview of Windows Defender Security Center
Windows Defender Security Center is a built-in security solution that comes with Windows 10 and 11. By offering a unified interface for overseeing and controlling security settings and configurations, it simplifies the process for users to ensure their device remains secure.
The Security Center allows users to view and manage security features such as antivirus and firewall protection, device performance and health, and family safety settings. It also provides security recommendations and links to relevant articles to help users stay informed and make informed decisions about their security.
The central security dashboard in the Security Center enables users to access all the security features in one place, making it easy to manage and adjust security settings. Users can quickly check the security status of their device and take actions to resolve any issues or threats detected.
Benefits of Windows Defender Security Center for Users
One of the major benefits of the Windows Defender Security Center is its ease of use. It provides a simple and intuitive interface that users can easily navigate, even without technical expertise. This makes it an excellent option for individuals and small businesses who may not have a dedicated IT team to manage their security.
Security Event | Description | Availability |
|---|---|---|
An attempt to trick users into providing sensitive information by posing as a legitimate entity through email, text message, or phone call. | Email protection, Safe Links | |
Malware infections | A software that is specifically designed to harm computer systems and networks. | Real-time protection, Scanning options |
Password theft | An attacker attempts to steal user passwords through phishing, social engineering, or other methods. | Multi-factor authentication, Security recommendations |
Insider threats | A person within an organization who has authorized access to data or systems and intentionally or accidentally causes harm. | Security recommendations, Data Loss Prevention |
Data leakage | The unauthorized transfer of sensitive information outside the organization. | Data Loss Prevention, Endpoint data discovery |
Rogue software | An application that disguises itself as legitimate software to trick users into installing it. | Controlled folder access, Application control |
Unpatched systems | Failure to apply security updates can leave vulnerabilities in the system that attackers can exploit. | Security update status, Security recommendations |
Public Wi-Fi risks | Using public Wi-Fi networks without proper security measures can expose users to cyber threats. | Network protection, Firewall |
USB threats | Inserting an infected USB device can spread malware to the system. | Device security, Removable device policy |
Social engineering | Manipulating users to reveal confidential information or perform an action that could compromise the security of the organization. | Security recommendations, User behavior analytics |
Overall, Windows Defender Security Center is an essential tool for managing security on Windows 10 devices. Its central security dashboard provides a clear and easy-to-use interface for users to view and manage their security settings, ensuring that their device is protected from various threats.
Best Practices for Security Management
In this final section of our Microsoft 365 for Enterprise Security series, we want to reiterate the importance of having a Central Cyber Security Dashboard for both IT and users. For more information on Enterprise Security, make sure to check out our blogs on Identity and Access Management, Threat Protection, and Information Protection. Having a centralized view of your organization's security posture is critical for identifying and addressing potential security threats.
To this end, we recommend implementing both Microsoft Defender for Cloud and Windows Defender Security Center. These two solutions provide a comprehensive view of your organization's security posture from both an IT and user perspective and offer a range of features to help you better manage and secure your environment.
With Microsoft Defender for Cloud, IT teams gain a centralized view of all security alerts and incidents and can easily manage and remediate potential threats. The central security dashboard provides real-time visibility into your organization's security posture, making it easier to identify potential risks and take corrective action.
For users, Microsoft Windows Defender Security Center provides a comprehensive view of their device's security posture, including antivirus protection, firewall settings, and more. Users can quickly see if their device is up to date and secure and take action to address any potential issues.
In conclusion, implementing a central security dashboard is a critical part of any effective enterprise security strategy. By using both Microsoft Defender for Cloud and Windows Defender Security Center, you can gain real-time visibility into your organization's security posture, and quickly identify and address potential security threats.
We hope you found this four-part series on Microsoft 365 for Enterprise Security informative and helpful. At Communication Square, we're committed to helping organizations implement effective security solutions that meet their unique needs. If you're interested in learning more about how we can help, and learn more about the benefits of partnering with a managed security service provider, please reach out to schedule a free consultation call.
Last Updated 1 year ago

